![[Top bar]](../../common/images/Topbar-en.gif)
![[Bottom bar]](../../common/images/Bottombar-en.gif)

by Frédéric Raynal
About the author:
Frédéric Raynal is preparing a thesis about computed image tattooing at
the INRIA (Institut National de Recherche en Informatique et Automatique). He is also involved in Bastille-Linux development.
Content:
|
Bastille-Linux
![[Illustration]](../../common/images/illustration166.jpg)
Abstract:
Released at the beginning of June, Bastille-Linux version 1.1 is not a new
Linux distribution but a set of scripts to better protect your system
against potential vulnerabilities. The authors approach is quite educational and
we can learn a lot when installing these scripts.
Introduction
With regards to security, Linux is much better than other operating
systems. Nevertheless, every distribution is different from the other one
concerning this matter. Bastille-Linux provides you with means to protect your
system. It was initially written for RedHat but the last version works with other
distributions too.
The project is managed by Jon Lasser (main coordinator)
and Jay Beale (main developer). Many other developers, software designers and
beta-testers are involved as well.
First of all, let's make it clear: Bastille-Linux is NOT a new Linux
distribution! It's a set of scripts, written in
perl intended to improve Linux security.
Security, means here computer security:
how to avoid that unwanted people access your machine? Bastille-Linux gives a
part of the answer by modifying the initial installation of your Linux distribution.
A basic task for every SysAdmin is to know the users needs, not only to
comply with them, but also to avoid to keep running network unused programs...
to be able to contain network security holes. One of my mentors used to say: the least
you do, the better ;-] Of course, he was talking about algorithm complexity, but
this is applicable to network administration: abundance of goods does harm as it
gives more attack places. To reduce vulnerability just install what you really
need.
Bastille-Linux tries to reduce the possibilities for an attack.
To reach this goal, the software designers have a very educational approach:
they explain what to do, step by step.
Presentation
At the moment of this writing, Bastille-Linux is in
version 1.1.0, released in the first half of June.
Apart from its obvious usefulness, Bastille-Linux is extremely educational.
The scripts ask detailed and acurate questions. Here, the developers try to teach the user. They explain the
question context and the results of the available answers. This makes
Bastille-Linux an easy to use tool.
For more advanced users, the source code, written in
perl, is a model of clarity
(yes, it's possible ;-) : every comment describes the way the action is working.r
Here are a few features of version 1.1.0 :
-
The scripts now work on already used systems
-
An undo function appeared :
every Bastille-Linux modified file is backed up to be restored if needed
-
Initially, Bastille-Linux was reserved for RedHat and Mandrake : this is not
true anymore. Now a module holds the right filepath according to the distribution on
which you run the scripts.
Bastille-Linux has different modules. Let's say 4 general modules and those
dedicated to particular purposes ( software such as
sendmail,
FTP,
... or like boot or useless daemons)
The general modules are used for:
-
Firewall installation
-
System software update
-
Audit on SUID-root programs
-
Deactivating and restricting useless services
The other modules concern more specific aspect. Some of them are dedicated to
security holes opened by bad configured software (sendmail or FTP
for instance), some others modify the configuration of a few services in a less
permissive way (PAM,
syslog,
...)
Some security functions cascade and offer different protection levels
(this is against my mentors principles ... but you have to emancipate one day ;-)
You must protect every service or every potential security hole by any means.
Thus, if one fails, the other ones keep protecting your system.
Installation or "let's go for a walk into the scripts while the wolf is not
there"
Previous versions of Bastille-Linux only worked on new systems this is not true
for the latest one. However, we must say what Bastille does is useless (almost) if
your system has already been used. Thus, it's recommended, for security reason
and not because of the software, to install Bastille-Linux on a new system
(freshly installed).
You've been warned, so let's go to the serious side: the installation!
Bastille-Linux is available as tarball .tgz
at bastille-linux.sourceforge.net.
This archive is only 134 Ko. Once downloaded, extract it
(tar
xzf Bastille-1.1.0.tgz).
Four scripts manage Bastille-Linux :
-
InteractiveBastille.pl : this script
asks the user various questions to determine what to do on the system.
Next, it creates a config file from the
given answers
-
AutomatedBastille.pl : installs
default configuration, offering the choice of using a firewall from a provided
configuration script. This script is not maintained anymore
-
BackEnd.pl : this one is in charge of
system changes. It gets its parameters from the answers you first gave.
-
Undo.pl : when you run
BackEnd.pl, a few system files
(/etc/syslog.conf,/etc/inetd.conf,
/etc/hosts.*,
...) are modified. To allow to restore in case of trouble, backup copies are
placed in the/root/Bastille/undo directory.
To install Bastille-Linux, you must be root since the scripts will modify
configuration files. Then, to install, execute
InteractiveBastille.pl first.
Next, answer the set of questions (detailed a bit further down). Last, run
BackEnd.pl
and it's done! A backtrace of the changes can be found in the
/root/Bastille/undo directory.
A few notes before you begin.
-
You're supposed to run the script from the
/root/Bastille directory
... this will change in a future version and then you'll be able to execute it
from any place (may be, it's already true by the time you read this)
-
Two modules allow account creation ... as soon as you installed shadow
passwords on your system. This is the default installation, but check that
/etc/passwd doesn't hold passwords,
that you must be root to access /etc/shadow
and that this last file really holds the passwords!
-
Bastille-Linux doesn't yet manage links between modules, like in kernel configuration
(this will be available in a future version). Take care of the answers given in
a module and to their consequences. Thus, you could tell IPChains module to
close port 2049 and keep NFS
in the list of active daemons from MiscellaneousDaemons module
(NFS uses this port).
Step by step
Let's have a look at the questions asked by Bastille-Linux to understand the different
steps. The letter between [ ] shows the default answer
(N -> No, Y -> Yes).
IPChains
This module is used to configure a firewall. Even if it isn't compulsory for
system protection, this allows to control network traffic from and to the
machine. The firewall traffic control is not enough, you must as well
reconfigure the daemons (remember, different security levels are not useless).
This script works in a very good way. It takes into account 2 network
interfaces: the one communicating with the outside, and the one communicating
with the local network. The goal is to determine the services available to the
machines and to stop the others. The default is to refuse everything coming from
the outside. Next, the script defines the rules to make some services available. Certains selected services.
The script manages TCP, UDP and ICMP protocols. It provides lists of services
to watch or to avoid for each protocol. It would be too long to detail here
Bastille-Linux approach to install a firewall, but reading the script and its
comments help a lot. However a minimum knowledge is required to use this
module.
PatchDownload
Updates are important to maintain system integrity. During the last few months, bind
and piranha, (for instance)
have had big security problems. They have been corrected quickly: with the source
code being public, some people immediately wrote patches.
Unfortunately, this script doesn't work very well.
It's rather complex since you must determine the installed packages, and among
them, the ones to updated.
Next, you must download the patch, check it hasn't been altered (either by
hackers or the transfer) before installing it. This really depends on the
distribution you use.
At the moment, Jay Beale recommends to manually execute this step but not to
neglect it. A more functional version of this module is under development and
should be available very soon.
FilePermissions
This module is based on a document from the SANS team. The aim is to determine
the programs only available to root (or root group member),
the ones needing to keep SUID bit, etc ...
-
Would you like to set more restrictive permissions on the administration
utilities [N] ?
Some programs must not be made available to everyone.
Bastille-Linux provides you with an impressive list of programs that can be
changed to rights 0750.
-
Next, it's about SUID bit. This bit allows a program to be run by a user having
root permission.
('s' in position 4, 7 and 10)
>>ls -l /bin/ping
-rwsr-xr-x 1 root root 17968 Mar 6
15:57 /bin/ping
This bit, it improves ease of use, reduces security.
That is, if one discovers a vulnerability (let's say a
buffer overflow ), he will be able to become root .
Bastille-Linux suggests to remove this bit from some programs among which
mount/umount,
ping,
dump/restore,
cardctl,
... Among others, this list contains ping
and traceroute that are two utilities
allowing to check a server state.
Removing their SUID bit corresponds to a paranoiac mode, but doesn't prevent
from the standard use of a machine.
In that list of SUID-root programs, you can find as well
the r-commands. It concerns programs
such as rcp, rlogin
or rsh. These utilities don't encrypt the
data sent to the network.
Furthermore, they only use the IP address as means of authentication.
This is inadequate (spoofing possibility).
AccountSecurity
Hacking often begins with user account (or system account) commitment.
A few simple steps make the task harder and allow to detect intrusion.
-
Would you like to set up a second UID 0 account [N] ?
Answering yes to this question creates another root account on your
system. In that case, you shouldn't use the original root
account anymore, but the one you just created. This gives twice more possibilities to
crack a root password... but allows you to see who uses the
root identity from the files in /var/log.
-
May we take strong steps to disallow the dangerous r-protocols? [Y]
As above mentioned r-commands
are a strong mean of getting a new account on a machine: the passwords are
transferred in clear text! On such a network, a sniffer offers interesting
aspects...
Bastille-Linux prohibits the use of r-commands
via PAM (Pluggable Authentication
Modules), removes execute permission and stops the servers found in
tcp_wrapper
(rlogind, rexecd and rshd). They are configured from /etc/inetd.conf
where you just have to put them as comments.
-
Would you like to enforce password aging? [Y]
Passwords then shall be changed every 180 days. Accounts where password
don't change are deactivated.
-
Would you like to create a non-root user account? [N]
Use your root account the least possible. As a matter of fact, a
single command like rm -rf
/ can make a disaster as root ... but a bit less as a standard
user. Only administrative tasks should be done as root.
-
Would you like to restrict the use of cron to administrative accounts? [Y]
cron allows to automatically run
tasks. For instance, an administrator can use it to check files integrity on a
regular basis, or to search the files in /var/log.
On the other hand, to give access to every user is too much of a privilege.
As a workaround, Bastille-Linux creates a file /etc/cron.allow
containing the users allowed to use this service.
BootSecurity
The options provided in this module concern the physical security of the machine.
This is to correct security holes of previous versions. Anyone having a physical
access to the console was able to get a privileged access (i.e. root).
Running LILO in single mode,
(LILO : linux single) allowed to get a
brand new shell belonging to root;-P
Obviously, that isn't enough. To physically protect a computer, the BIOS must
be password-protected, the hard disk must be the only boot device, the box must
be locked to prevent someone from adding his own hard disk...
This is of course the paranoid behaviour and you don't need to do that without a
very good reason.
From a sofware point of view, some restrictions provide a good compromise
compared to the above mentioned:
-
Would you like to password-protect the LILO prompt? [N]
Answering "Yes" prevents unallowed people from accessing the system after
reboot.
-
Would you like to reduce the LILO delay time to zero? [N]
That way, someone is unable to provide parameters at boot time.
If your computer is running various OSes, you must not do this, since the
default OS would be the only one working!
-
Do you ever boot Linux from the hard drive? [Y]
If you answered yes to one of the previous questions and LILO is installed
on your disk, then you must also answer yes to this one to write the LILO
changes on the disk.
-
Would you like to write the LILO changes to a boot floppy? [N]
If you own a boot floppy, either for emergency reason or because it's your
way to boot Linux, then you must change it.
-
Would you like to disable CTRL-ALT-DELETE rebooting? [N]
This is intended for preventing someone from rebooting the machine.
However, this is useless as soon as the electrical plug is not protected ;-)
-
Would you like to password protect single-user mode? [Y]
As we already saw, it looks like a good idea to prevent any people from
becoming root on the machine.
SecureInetd
The goal of this module is to restrict and deactivate superfluous services.
Hackers are easily able to find security holes in any privileged service, then
you must restrict both service and privilege.
For instance, a mistake in RedHat6.0 DNS allows to remotely become root.
Deactivating this service or reducing privileges protects from this annoyance.
Some protocols, such as the already mentioned r-commands
but ftp
or telnet too, are quite vulnerable.
Others allow to get information (finger
or identd for example) on the machine
accounts, etc ... Many of these services are managed by
tcp_wrapper
which allows to control who accesses a given service (by means of
/etc/hosts.{allow,
deny}) files. Then, once the wrapper decided the client was allowed to
access the service, it sends the request to the corresponding server.
This part is still a bit rigid and should be changed in future versions.
-
Would you like to modify inetd.conf and /etc/hosts.allow to optimize
use of Wrappers? [Y]
Bastille-Linux installs those two files.
It can be interesting to have a look at them as to pass them more
accurate parameters according to your needs.
-
Would you like to set sshd to accept connections only from a small list
of IP addresses? [N]
sshd is a daemon allowing to connect
in a secure way (keys exchanging, passwords and data crypting, ...).It's
a full replacement for telnet,
rlogin,
rsh,
rcp
and ftp. Let's mention an equivalent
version to ssh
under BSD license: OpenSSH.
Back on this later.
-
Would you like to make "Authorized Use" banners? [Y]
Every person trying to connect to your machine will see a warning message
asking if she's allowed to connect through this service.
This message can be found in the /etc/motd file.
Before continuing, let's remember that the network relies on a client-server model.
Thus, you must know if you are on the client side or on the server side
of each service. For instance, stopping the web server doesn't prevent you from
browsing the web: your browser is a client.
DisableUserTools
This short module, is essential on a server.
Usually, a hacker accesses a machine using a normal user account. Then, he
recompiles a few programs on that machine to exploit its weaknesses.
This module deactivates the machine C compiler for every user but
root.
Then, if this machine is only a server on which no one has to compile
anything, remove the compiler.
ConfigureMiscPAM
The aim of this module is to limit the risks of Deny of service attacks
- these attacks freeze a system overloading it (ie: to fill a partition with
core files,
ping of death, etc ...)
PAM stands for "Pluggable Authentification Module". It's a library allowing
the SysAdmin to select the type of users authentication for each application,
the rights they have, the resources they can access, and so on.
-
Would you like to put limits on system resource usage? [Y]
The /etc/security/limits.conf
file contains system limits. Bastille-Linux changes them that way:
-
core files are limited to 0 ;
-
each user is limited to 150 processes ;
-
the maximum file size is limited to 40Mb.
Each value can be modified later directly from the configuration file.
-
Should we restrict console access to a small group of user accounts? [N]
On RedHat6.0/6.1, users connecting from the console have some privileges
such as mounting the CD-ROM. It's possible to restrict the console access to a
group of trusted users. This question allows to define those users if you feel
like implementing such a policy.
Logging
syslog is one of the most important
services to detect if a machine has been commited.
This daemon records some system events. You can choose to change the level of
recorded information.
It's remarkable that if you have a minimal number of running services, every
problem will be pointed out quickly from /var/log files. On the other hand, if your system runs a lot
of useless servers the
/var/log files become very big and
accordingly more difficult to manage (you then need to implement dedicated
scripts).
This module adds new checks in the /etc/syslog.conf file.
-
Would you like to add additional logging? [Y]
Bastille-Linux creates a /var/log/kernel file, for messages coming from the kernel
and recording serious problems (firewall messages make part of this category).
Some information is sent to 2 terminals (TTY 7 and 8). A new file named /var/log/loginlog records users connecting to the system.
-
Do you have a remote logging host? [N]
Unless you own another machine to which you can send your messages, the answer
is no.
-
Would you like to set up process accounting? [N]
Under Linux, it's possible to record the executed commands, who did it and
when. If it's useful to check the machine activity, this log quickly becomes
enormous. Of course, it uses a lot of resources and it's then better to
deactivate this feature unless you really need it.
MiscellaneousDaemons
Always in the concern of minimization, this module only activates the servers
you really need at boot time. As a default, almost every service is useless and
so deactivated. You can reactivate a service with the chkconfig command.
| Services |
Description |
| apmd |
Used to control laptops batteries. |
| NFS and samba |
To manage shared file systems ... even if quite useful on heterogeneous
networks they are big security holes. |
| atd |
Everything atd does can be done with
cron. too. |
| PCMCIA services |
If you own PCMCIA hardware, what is quite common on laptops but rather
unusual on workstations. |
| dhcpd |
Server used to provide temporary IP addresses. This kind of service is
either "offered" by Internet Service Providers (ISP) or used on a local network.
|
| gpm |
Used while in console (text) mode to manage the mouse. Unless you often work
in console mode, this service is useless. |
| news server |
Very few people need to run a news server on a machine ... usually, it's the
ISP job. |
| routed |
As for the news server, it's the ISP job: it concerns your DNS. |
| NIS |
Very useful service on a local network ... but origin of big security
problems!!! |
| snmpd |
Server dedicated to network administration (statistics, management,
users,...) |
| sendmail |
There is no need to run it as a daemon to allow you to send or receive mail.
Furthermore, if you get your mail from your ISP through POP or IMAP, sendmail
is useless and since this program has big security holes... |
Sendmail
As previously mentioned, sendmail
is a service to manage mail. Its history is full of security holes caused by the
many tasks a mail server has to manage and the necessary privileges to achieve
them (name resolution, syslog information, etc...).
Apart from its weaknesses,
sendmail allows to get information about
a specific user on a given server.
For instance, sendmail
EXPN and VRFY commands allow
someone to know if a specific user account exists.
sendmail as we said before, doesn't
need to be run as a daemon to send and receive mail. For home users sendmail
is probably quite useless since you can use any mail client
(netscape, rmail,
pine,
mutt,
etc...) to send your mail. To receive your mail, you can activate
sendmail
on a regular basis to check your mailbox.
-
Do you want to leave sendmail running in daemon mode? [Y]
We have just seen in most cases it's useless and dangerous, then it's
much better to deactivate it.
-
Would you like to run sendmail via cron to process the queue? [N]
Using this, sendmail
checks the mail queue every 15 minutes.
You can change this parameter from the /etc/sysconfig/sendmail file.
-
Would you like to disable the VRFY and EXPN sendmail commands? [Y]
These commands provide useful information to hackers or for spamming.
RemoteAcces
It's often useful to be able to connect to a remote machine. We have seen that the r-commands
allow this in an insecure way. Bastille-Linux suggests to download
ssh.
It's a software encrypting the data (and so the passwords) transferred through a
connection.
You can use a software in which the session key length doesn't exceed
128 bit. Let's explain what a session key is. It's the key used to crypt the
data. This session key is built step by step by the client and the server:
it comes from a key exchange protocol (Diffie-Hellman in most cases). It
consists in building a key from a piece of every member's key. Next, this
session key is used to crypt the data according to a symetric algorithm
(i.e. the same key is used to encrypt and uncrypt the data). Thus, DES,
used to encrypt Unix passwords, is a symetric algorithm with a 56 bit key.
Now, is a 128 bit key big enough to ensure transaction confidentiality and
security: YES! Even if today DES is said "not so secure", the best attacks are
not within range of CPU power that most people have. On the other hand, it's a mistake to believe a
key of 2k length is twice more difficult to find than a key of
k length. As a matter of fact, if the difficulty is exponential, it grows
much faster than the key size. For a key of k length, it exists
2^k possible keys (and so 2^2k for a key of 2k length). Then, multiplying
the key size by 2, we add
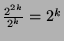 possible keys! When you notice the difficulty to break DES (56 bit), you can
expect 128 bit keys to be inviolable (as soon as the encrypting/uncrypting
algorithm doesn't hold security hole). From an attack point of view,
to increase this limit only makes the difficulty go from an "impossible
level" to an "even more impossible level".
possible keys! When you notice the difficulty to break DES (56 bit), you can
expect 128 bit keys to be inviolable (as soon as the encrypting/uncrypting
algorithm doesn't hold security hole). From an attack point of view,
to increase this limit only makes the difficulty go from an "impossible
level" to an "even more impossible level".
4 different software packages provide with similar services :
ssh 1.2.x : a client-server system to
establish encrypted connection.;
ssh 2.x : the same as the previous one
but with less weakness and more possibilities;
OpenSSH : a similar version to the
previous one but under BSD license;
ssf : like ssh,
but accepted by French law. (This had to be said!)
The following modules still concern services. For them the policy may look
surprising: you begin with privileges restriction and then you stop them.
In spite of appearances, these two measures are not conflicting. These services
can be reactivated, either incidentally or by undesirable people... then it
seems better to restrict them.
DNS
A DNS (Domain Name Server) allows to link an IP address and a machine name and
vice versa.
For instance, the address 198.186.203.36 corresponds to www.bastille-linux.org.
The main function of this server is called BIND. Lately, a DoS type attack against
BIND has been found. You can avoid it only giving DNS access to a small group of
directories (you can change the root directory - default to / - with the
chroot command before executing a
command or a script).
Let's add a few technical details before explaining Bastille-Linux behaviour.
The daemon managing this service is called named.
Its configuration comes from the /etc/named.conf file.
-
Would you like to chroot named and
set it to run as a non-root user? [N]
To do that, Bastille-Linux creates a new user called
dns, who has no shell, but his own directory /home/dns.
In that directory you build a classical system architecture adding usual
directories (/usr,
/etc,
/var,
etc ...). Next, you have to copy configuration files and libraries needed by the daemon.
Some more changes have still to be done
(for syslog
for example - check the script DNS.pm).
Now, the DNS has its own environment :)
-
Would you like to deactivate named, at least for now? [Y]
Most people don't need a name server on their machine, as the ISP provides
them with this service. The DNS-HOWTO describes cache installation for name
resolution, but even that can be a source of problem.
Apache
Apache is the most used web server on
the Internet. Such a server is only useful in two cases:
-
to host a site: for this you need a fixed IP address. ISPs have such addresses
but it isn't normally true for their clients
-
to check your own web pages: in that case, you just have to launch the server
(/etc/rc.d/init.d/httpd start) when
needed.
The configuration file sfor this daemon can be found in
/etc/httpd/conf.
-
Would you like to deactivate the Apache web server? [Y]
Since we don't always need it and in a minimization spirit, we deactivate
it.
-
Would you like to bind the web server to listen only to the localhost? [N]
It's possible to bind the daemon httpd
to a specific address. Here, Bastille-Linux suggests to connect it to the
localhost address,
127.0.0.1. This allows to have a server running on a machine to test your own
web pages.
You can access them from:
http://localhost/ (or http://localhost/raynal
to access my own pages)
That is Apache uses the
loopback interface
(lo) to work.
-
Would you like to bind the web server to a particular interface? [N]
Answering yes cancels the previous answer.
We said there we wanted to use the web server with the loopback
... and this question allows to give another interface (Ethernet for example)
with an IP address bound to it.
-
Would you like to deactivate the following of symbolic links? [Y]
You must do that. As for the DNS working in a restricted space, you must not
allow Apache to leave its universe
(i.e. /home/httpd). For instance,
if one of the users has a link to root / in his web server directory, then everybody can access
all the files... especially the configuration files such as
passwd and others.
-
Would you like to deactivate server-side includes? [Y]
As Jay Beale says, if you don't know what it is, you don't need it!
Enough to say that this can be configured as to allow users to execute any
program on the server (I'm afraid so... fear that sysadmin friends... that was a
dream for you ;-)
-
Would you like to disable CGI scripts, at least for now? [Y]
Writing a CGI script (Common Gateway Interface) is not so difficult ... but
implies to be careful (for instance to avoid stack overloads generating core
files on the server). Many methods used to commit a system rely on errors in
these scripts.
-
Would you like to disable indexes? [N]
Without index.html file in a directory, Apache lists all the files
in that directory. This is less a problem than allowing symbolic links
reading... but, just imagine if a directory contains sensitive data.
A web server as any other server, can become a true invitation to visit your
machine, perhaps to damage it, if it is badly configured. This can become a bit
annoying in some cases. Let's say a bank for instance, if the customers names
are readable (perhaps their passwords)... just go and visit
www.kitetoa.com,
you won't regret it ;-) ( Translator's note: Unfortunately, French only!)
Printing
Only one question: will you be printing from your machine?
If the answer is no, Bastille-Linux deactivates the
lpd daemon and removes the
SUID bit from lpr and lprm.
=============
FTP
From a security point of view, FTP
can be the source of many problems. For example, when initiating a connection,
passwords are transferred in clear text. The same holds for the data, it is dangerous if
it is sensitive data (financial or medical data...)
Furthermore, lately security holes have been found in
wu-ftpd. If you need to leave that
server running, Bastille-Linux allows to restrict some features.
The file managing the FTP server
access is /etc/ftpacces.
-
Would you like to disable user privileges on the FTP daemon ? [N]
One of FTP problems is to allow anonymous connection
(you know, that user having an email address as a password... very often a ghost
one ;-). An other problem is file upload (i.e. to send files to the server and fill the disk or upload programs to break into the server). Many attacks use
these weaknesses.
Another trouble comes from the fact the transaction is not encrypted.
-
Would you like to disable anonymous download? [N]
This prohibits connection to your server with
anonymous login.
A few more tricks and tips
As I said before, Bastille-Linux is a great educational tool.
Questions and comments are meaningful.
When things are not so clear, many resources are available to find the right
answer. The best way to learn about a given subject is to use the desired module.
To do that, just backup the file containing the questions. Next, edit the
Questions.txt file. Every module begins with the FILE keyword... just keep what
you need.
/root/Bastille >> cp Questions.txt
Questions.txt-orig
/root/Bastille >> emacs Questions.txt
BackEnd.pl &
/root/Bastille >> ./InteractiveBastille
Of course Bastille-Linux measures are not enough to secure your system:
- no system is 100% secure;
- more measures are required to complete Bastille-Linux "work".
Among these measures you can think of are log file analyzers, port scan detection
(portsentry, snort, snplog, etc ...), using www.openwall.com kernel patch (non executable stack,
directories /tmp and /proc rights restriction, etc...).
It's a long and difficult way to secure a system. You must keep your self informed about
security holes (by means of mailing lists such as bugtraq from securityfocus
site, for example).
Conclusion
Bastille-Linux helps to secure a well known distribution
. You could say: "then why use this one?"
Sure ... but RedHat (Mandrake - they are quite similar) has some nice features.
The aim of this article is not to promote (or to blame) a distribution.
After all, the freedom of choice is one of the strength of free software.
As a matter of fact this article has various goals.
First, to show you the permanent worry of a sysadmin who lives in fear
of seeing his network destroyed by some people yearning for shivers.
On the other hand, this tool allows you to deeply visit the configuration of a
Linux system. In this perspective, it's a good way, not only for newbies but
for advanced users too, to discover the mystery of Linux configuration.
The two fundamental and general concepts are minimalism and depth.
Less running services means less security holes.
For each of these services, various protections are better than one... but this
is double-edged since a bad configured protection (or the conjunction of
various) can turn against you.
Last, let's mention the next version will be named BUS (Bastille Unix
Security). It will be a clever mixture of Bastille-Linux and Msec (Mandrake
Security Project), the later one being renamed to Usec (Unix Security Project).
References
-
http://bastille-linux.sourceforge.net
: Bastille-Linux official site
-
Bastille-Linux: A Walkthrough : on www.SecurityFocus.com site,
by Jay Beale, main author of Bastille-Linux,
presents the software and its installation. It helped me a lot to write the
article you are reading ;-)
-
http://www.sans.org : the site of the
SANS group, (Jay Beale collaborates with them). A true information mine
about computer security.
-
http://www.securityfocus.com/frames/?content=/vdb/stats.html:
still at SecurityFocus, an interesting study about OSes and their bugs.
OS et leurs bugs. First places are for a well known "OS" family, next comes
Linux.
-
www.kitetoa.com : a site testing web servers...
and finding interesting things. At the same time funny and pathetic (for
sysadmin caught in the act) -French only-
-
http://www.ssh.com : secured
shell. ssh official site; freely usable for evaluation or non commercial use
or for universities
-
http://www.openssh.org : same as ssh ...
but under BSD license :)
Last modified: Mon Jun 12 16:40:50 CEST 2000
Talkback form for this article
Every article has its own talkback page. On this page you can submit a comment or look at comments from other readers:
2001-01-27, generated by lfparser version 2.8

![[Illustration]](../../common/images/illustration166.jpg)

![]() possible keys! When you notice the difficulty to break DES (56 bit), you can
expect 128 bit keys to be inviolable (as soon as the encrypting/uncrypting
algorithm doesn't hold security hole). From an attack point of view,
to increase this limit only makes the difficulty go from an "impossible
level" to an "even more impossible level".
possible keys! When you notice the difficulty to break DES (56 bit), you can
expect 128 bit keys to be inviolable (as soon as the encrypting/uncrypting
algorithm doesn't hold security hole). From an attack point of view,
to increase this limit only makes the difficulty go from an "impossible
level" to an "even more impossible level".